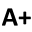In this assignment, you are acting as a network security consultant for the company in the case study below. You are to write a report for this company’s CEO, outlining what network security risks may exist, how these may affect this company, and what technology should be adopted in order to reduce the risk of it happening. You are to refer to cases which have happened in the past to other businesses and describe how they may affect this business. I would suggest discussing at least 2 or 3 categories of attacks, maybe grouping many examples into these categories. For example, if you were to discuss a SQL database attack, this would be the category and you should present 2 or 3 documented cases of it happening to other real businesses. You should then highlight how this attack may affect the case study business (if they don’t have a database that might be difficult) and what effect it might have; on prices of products being changed for example. Following this, you would then outline a possible solution for preventing it. If your two categories of security attacks can be mitigated through the same solution, you only need to present it once. The document should be approximately 1500 words, written in a professional report style and include all of the references of the previous security attacks. The report MUST be related to the case study below and if you simply present a collection of security attacks, you will be significantly marked down.
Case Study
Company A is a medium sized food manufacturer based in Kuala Lumpur. They sell and manufacture a range of foods which are sold locally and exported to various markets throughout the world. The company has seen significant growth within the past few years with the introduction of their online sales website. Its office consists of 3 departments: Sales, Engineering (manufacture) and Finance. It has Sales and Finance office in Singapore located 350km away from Kuala Lumpur and hosts 50 employees. 2 The following topology illustrates the network architecture and topology of the Kuala Lumpur office of Company‐A and Singapore Company‐B. The Singapore Office is small and only has 50 workstations used by sales and finance staff. These are connected to a distribution switch which is directly connected to the branch router. All of the Singapore Office traffic is routed through to KL office and processed there. The Kuala Lumpur office has simple network architecture. Clients workstations are connected to an access switch, then connected to a distributed switch and then to the router’s inside interface. All clients at this site are in the same subnet. The internal routers’ second interface connects directly to the internet service provider (ISP) router. The third interface on the internal router has a demilitarised zone (DMZ) hosting several servers. These servers include web, email and FTP applications. However at this point, the DMZ has not been configured. All of the workstations are running Microsoft Windows 7 SP1 and it is left up to the user to determine the update of patches. The servers are all running Windows Server 2012 and have been installed using the default setup. The webserver is running Microsoft IIS and hosts all of the company’s external facing websites including their online ordering and payment system. The webserver also has a number of pages for internal staff (password protected) which has the recipes for the company products. This same server also holds all the customer information in a SQL server database. The FTP service is also enabled on this server so IT staff can update and access the webservers files and database. The company also hosts its own email server and this is provided by Exchange Server 2010. Sales reps out and about are able to access their email via OWA, desktop and mobile devices. DNS server is provided by Windows Server 2012, along with Active Directory and username and password authentication. All of the networking devices are CISCO and the IOS, which was shipped (2013) with the devices, was used. The DMZ is provided by a CISCO ASA and again, the default IOS is used. The company also has a number of android mobile phones which are used for accessing the internal webserver and email server. These are used by all staff inside and outside of the network